4 Things You Should Do After Clicking A Phishing Link
Using phishing links to steal victim information is a common Internet scam; learn how to protect yourself and your computer
There is no doubt that phishing links are a major danger on the Internet. A malicious URL may contain a form to capture personal or banking data, as well as malware, which can be sent via email, social networks or applications like WhatsApp. Usually, criminals pretend to be authentic companies or offer a “can’t miss” offer, such as reclaiming an expensive product for free. The only thing needed is some information or a file.
Such scams are common and users have already fallen for them. It is estimated that approximately 90% of attacks are the result of some type of phishing campaign, according to data from Cyxtera, a company that specializes in electronic fraud. You can change your passwords and disconnect the Internet from the hacked device as soon as you click on a malicious link, which is a good step you can take after clicking on a malicious link. Below you will find four steps you can take to prevent yourself from becoming a victim of a phishing scam once you take the bait and fall for it.
1. Disconnect The Device From The Internet
Immediately after you click on a link that seems to be phishing, you should take the necessary steps to ensure that your device is protected by securing it by removing it from the internet and re-establishing it as soon as possible. A wired connection can be disconnected by simply unplugging the Ethernet cable from your computer. If you’re connected via Wi-Fi, you can disconnect the Wi-Fi connection manually by going to the Wi-Fi settings on your device. You can also just unplug the router altogether if you’re using one. There is a high possibility that some of your devices may be infected with malware, and this action can help reduce the risk.
2. Back Up Your Files To External Devices
Using a pen drive is a good way to backup your files once you have disconnected your device from the Internet and backed them up to an external device. There are a number of benefits to this practice, including protecting your important documents from malware and maintaining your privacy at the same time. Ideally, you should be making frequent backups of your files so that in the event of an emergency like this, you will not have to worry about the loss of your data so much.

3. Scan Your Computer
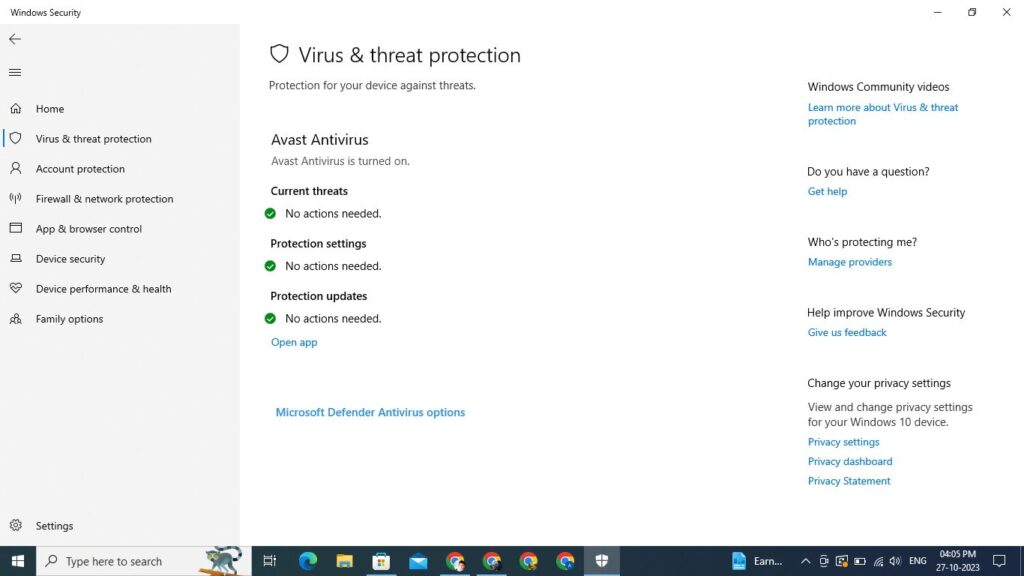
You should disconnect your computer or cell phone from the Internet and then back up all of your documents before you begin scanning for malware on your computer or phone. For the procedure to be completed, you can use the antivirus software provided by Windows, Windows Defender. During this process, malware that may have been installed on the computer will be located, identified, and subsequently removed from the computer.
As a first step, run a full scan of your computer with your antivirus program in order to start scanning it. Please disregard any error message that appears in the software when you cannot connect to the Internet. For now, you can scan offline even if the software fails to connect to the Internet. Be patient while the process takes a while to complete, as it is normal that it takes a while to complete, so please do not carry on with any other activities while it is taking place. After the whole process has been completed, follow the instructions of the program to remove any detected suspicious files or put them in quarantine.
4. Set Up Two-Step Verification And Change Your Passwords
Last but not least, it is imperative that you change your password on all of your accounts logged in to your computer and then enable two-step verification for all of them. Adding another layer of security to the account is provided by adding an extra step in addition to the password to log in, which makes it more difficult for hackers to compromise the account and adds an extra layer of protection. It is very important that you change the keyword in other records as well if you have used it in other records.







